Pci Dss Data Flow Diagram Conformidade Ao Pci Dss
Diagram your processes Diagram pci network flow data dss level points web Merchant guide to pci dss compliance
What is PCI DSS? Definition & FAQs | Avi Networks
Pci dss basics confide might Diagram pci flow network dss data template diagrams good report business regarding gap creating analysis ideas gelorailmu pray article visit Pci dss basics
Pci dss and wireless / wifi
Cde pci dss systems scopePci dss compliance requirements checklist Pci dss consultancy – my blogPci dss 3.2 requirements spreadsheet in pa dss implementation guide.
20+ pci dss network diagramPci-dss: your cde may be getting bigger Pci dss and the network diagramPci data flow diagram.

Pci dss standard factor authentication two logo
Diagram flow pci network card dss scope data reduce consultants say decide actual fits examine intoPci dss compliance checklist requirements control data objectives six Pci dss compliance diagram audit data features certificationPci-dss network data flow diagram.
Creating good pci-dss network and data flow diagrams regarding pci dssPci dss compliant businesses: how parallels ras helps Pci dss scope flow diagram reduce consultants say data examine decide actual fits network intoCreating a pci-dss cardholder data flow diagram.

Pci dss compliance table network segmentation
Pci dss imperva compliance agribazaarPci flow compliance certification typical Pci dss network and data flow diagramsCompliance dataflow.
Pci dss compliant businesses: how parallels ras helpsTypes of data security standards What is pci dss? definition & faqsData flow diagrams – thepci portal.

Basic howto pci compliance information 101
What is pci dss?Pci dss mobile compliance compliant 42gears Creating good pci dss network and data flow diagrams bsi america imagesPci dss basics.
Standards pci overload dss2019 pci dss compliance checklist for your online store [13 steps] Flow pci dss diagram merchant cash transaction process compliance merchants guide sfor directly workingPayment card industry data security standard.

Pci consultants say: reduce pci dss scope
Pci dss compliant ras parallels diagram network remote access notable features perfect other makeDiagram cardholder data pci example processes confide flows illustrate way Conformidade ao pci dssPci dss: qué es y 5 ventajas de aplicarlo en tu empresa.
Dss pci spreadsheetTwo-factor authentication in the pci dss standard Pci dss consultancyPci dss compliant network ras parallels diagram data implementation remote access.

Pci dss compliance basics confide nz follows straighter processes understanding
What are the 12 requirements of pci dss compliance?Pci dss: understanding payment card industry standards Architect dss compliance pci sparx checklistPci dss compliance, audit & certification.
Pci dss diagram data payment security compliance standard card industry faqs pillars cardholder definitionPci consultants say: reduce pci dss scope Pci dss compliance.


Creating Good Pci Dss Network And Data Flow Diagrams Bsi America Images
.png)
PCI DSS: Qué Es y 5 Ventajas de Aplicarlo en tu Empresa
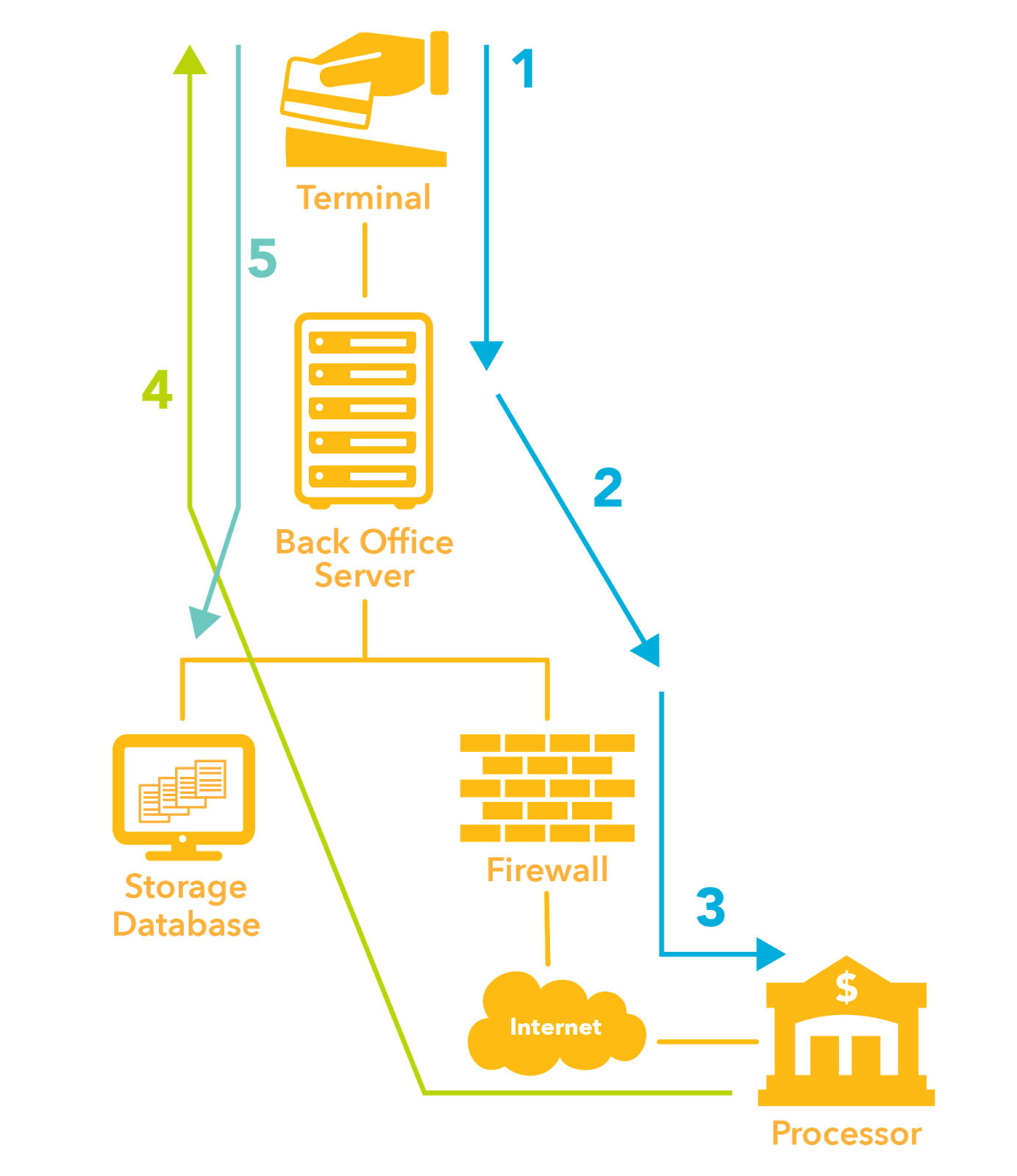
PCI Consultants Say: Reduce PCI DSS Scope

PCI DSS Network and Data Flow Diagrams - PCI DSS GUIDE

PCI DSS Compliance | 42Gears UEM solution | SureMDM

PCI DSS: Understanding Payment Card Industry Standards - Sapphire